The industry-wide demand for cybercrime fighters is not diminishing anytime soon, with employment growth for these IT specialists outpacing the occupational average by more than 400%. But in no way does this job windfall lessen the importance of an exceptional cyber security cover letter when pursuing the hottest, best-fitting opportunities.
No matter how secure anyone’s career prospects are, keeping up with today’s job search and hiring practices is always advisable. Resume.io’s online resources were created with that in mind. Our growing collection now includes more than 180 occupation-specific cover letter examples, paired with step-by-step writing guides.
Central to this guide is a cyber security cover letter sample that you are welcome to adapt for your own job application. Section by section, the sample wording illustrates our tips on how to craft an interview-winning cover letter. Topics we’ll discuss:
- The best format for organizing your cyber security cover letter
- Understanding the strategic angle for each cover letter part: header, greeting, introduction, body, and conclusion
- Safeguards for an error-free cyber security cover letter
Best format for a cyber security cover letter
The logical simplicity of a cover letter’s format might seem like a refreshing change for someone whose practical and tactical knowledge of complex IT infrastructure is so sophisticated. Across all occupations, the framework of interconnected components is consistent:
- Cover letter header
- Greeting/salutation
- Introduction
- Middle part (body)
- Closing (conclusion and sign-off).
Conforming to this stepwise outline will help keep your cyber security cover letter on track while hitting the mark for brevity and completeness. Cover letters should never take up more than a single page. And no cheating to squeeze in more text by shrinking your font size! That means the word count should never exceed 400.
The same “less is more” principle applies to a cover letter’s overall appearance. At first glance, it should look clean, streamlined, polished, and inviting to read.
- Fonts can still be attractive and modern-looking, as long as they are legible, large enough, and easy on the eyes.
- Strike the right black-and-white balance with optimal cover letter spacing including ample margins and possibly bullet points highlighting key qualifications.
- Formatting flourishes, perhaps graphic accents, and color splashes in the header should be sparing. The impact should be attractive without distracting.
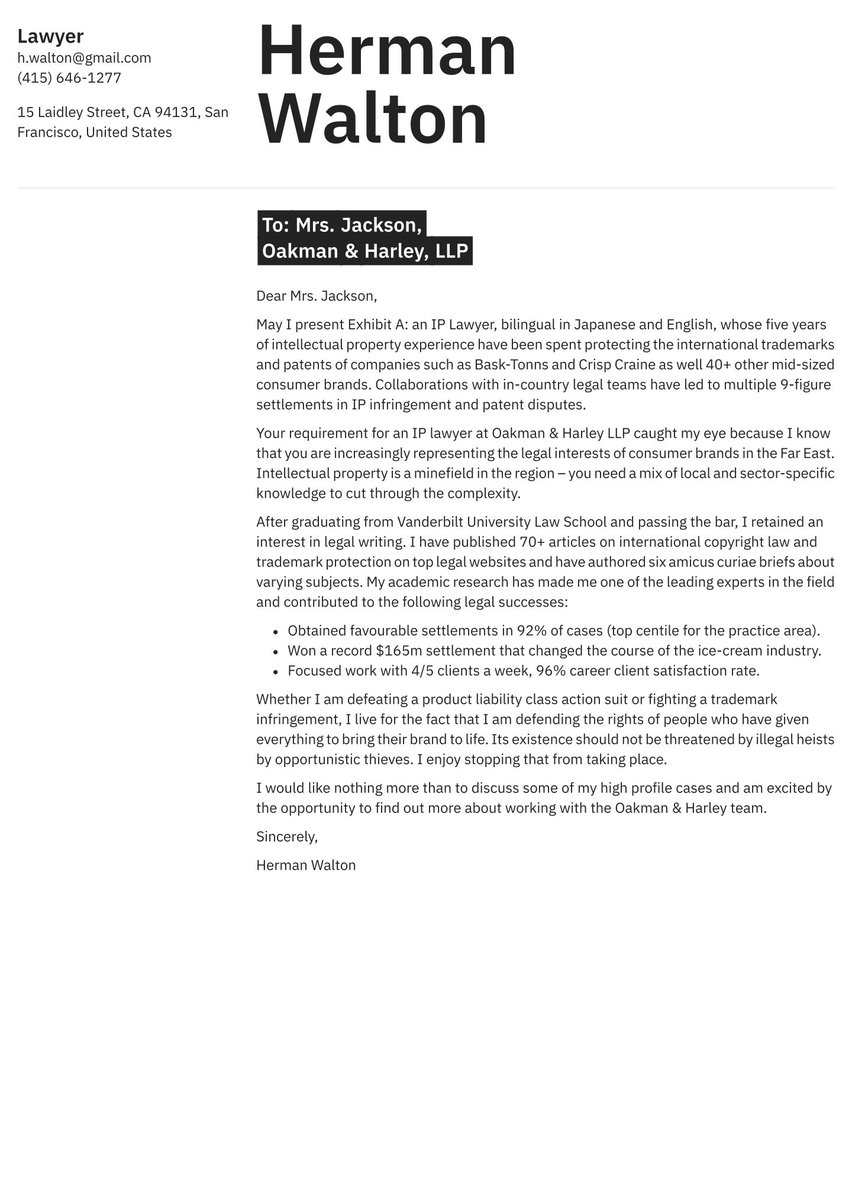
Strategically speaking, for every cover letter part, there’s a persuasive purpose. That will become clear as we walk through the segments one at a time. But first, here is an adaptable cover letter example for a cyber security expert. You can modify some or all of it to suit the position and employer.
Dear Mr. Warwick,
With five years of system administration, network optimization, and cyber security experience at two blue-chip organizations, I am ready to take the step to a consultancy role.
While much of my career thus far has focused on troubleshooting and risk management, I have enjoyed lead roles in major strategic projects. For example, we reduced downtime due to cyber-attacks by 35% thanks to an employee awareness course. Cyber security is as much about influencing behaviors as it is about fighting malware and hacks. Embedding such behaviors is a critical approach for any consultancy.
I am an experienced trainer in all aspects of operational cyber security and enjoy passing on my knowledge to others. I have run 200+ training sessions and enjoy shocking attendees with real-world examples of what happens when cyber security goes wrong. I wish to join a consultancy because it allows me to widen my impact.
My complete certifications and qualifications are outlined in my resume, but the following should offer a reasonable window on my proficiency:
Knowledge: Anti-Virus, RSA security, ID/PS, Full Packet Capture, Host-Based Forensics
Certifications: SANS GIAC/GCIA/GCIH, CISSP, and SIEM-specific training
Architecture: Nitro/McAfee Enterprise Security Manager, ArcSight, QRadar, Splunk
Signature development: YARA, Snort, HIPS
Every project that I have led has been run on agile principles. I have enjoyed the intellectual challenge of working out seemingly impossible problems. One of our projects was even nominated for “Process Improvement of the Year” by CyberTech magazine.
I am excited to learn more during a potential interview and look forward to hearing about what you hope to achieve with your clients over the coming years.
Sincerely,
Landon Parks
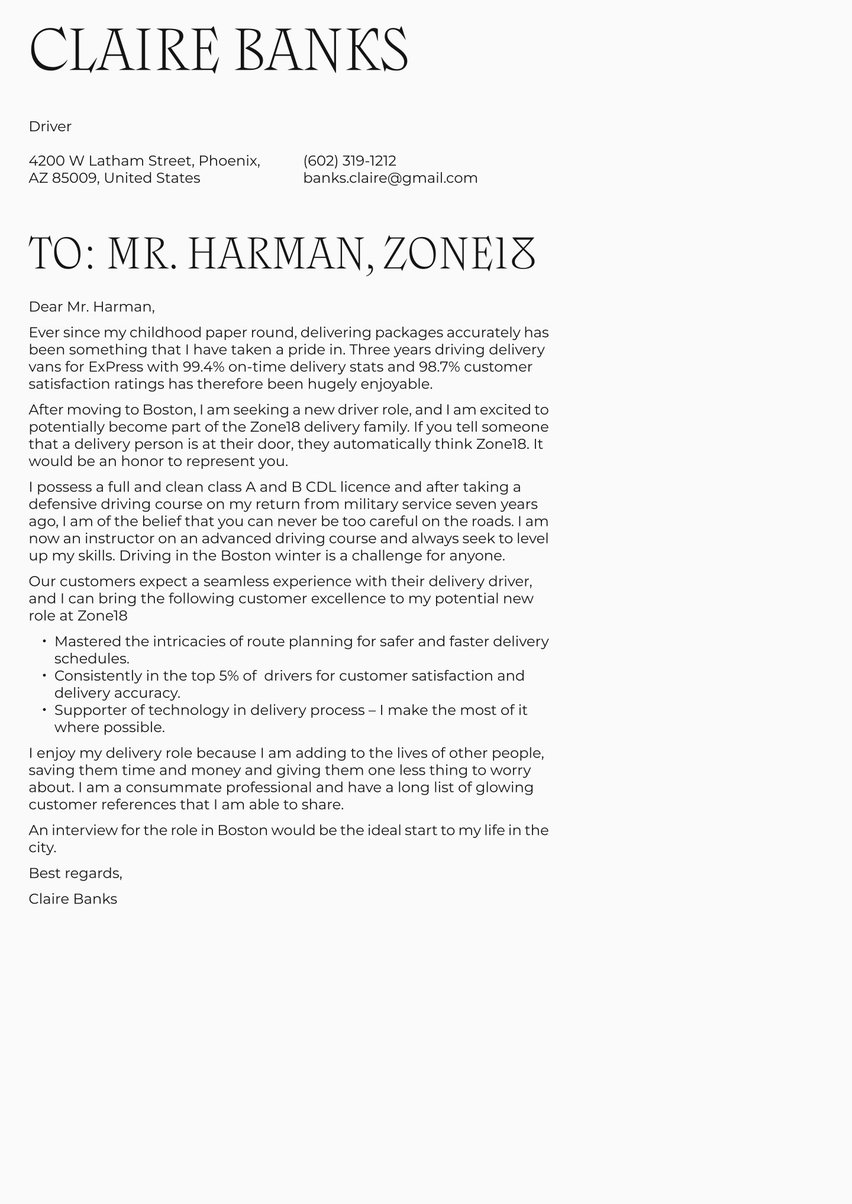
Cover letter header
The practical and esthetic value of an eye-pleasing header design should not be underestimated. Off the top, it visually distinguishes your job application from the others. Wherever your cover letter lands on any recruiter’s desk or digital screen, it is instantly identified as yours. This makes it easy for duly impressed hiring managers to contact you for an interview. You might score extra communication points for the obvious lengths you went to portray a professional and accessible image. Recruiters will be especially impressed with your attention to detail if the design elements of your cover letter and resume are aligned in the headers and elsewhere.
As a document label, the header draws the reader’s eyes to where your name, occupation, and contact information are displayed prominently. The adjacent white space offsets the denseness of your letter’s body text, for an overall reader-friendly impact.
So cyber security job candidates can take some leeway in breaking the geek mold without going too crazy with creativity. An understated version of stand-out is the look to strive for.
The goal of the cover letter header: Distinguish yourself from other cyber security candidates with identification information that’s eye-pleasing and easily found.
Cover letter greeting
An unfortunate, but all too common, approach for seemingly less-motivated job seekers is to blast off a slew of generic applications en masse, “just to see what happens.” Recipients can readily pick up on the sender’s apparent lack of interest and obvious lack of effort.
A customized cover letter, geared to the specific job and hiring organization, sends the opposite message — that you are serious about your job search. And the first indication that you’ve gone to the trouble of researching both the position and employer is the personalized cover letter greeting.
Addressing the recipient by name is not only the most professional and personable way to start off but also more likely to prompt a response. Research has proven that people like hearing and reading their own names.
The traditional “Dear Mr. / Ms. Surname” is timelessly appropriate. It’s polite and businesslike without being too stuffy. No recipient should take offense — as long as you’ve double-checked the gender and name spelling. There are times when the less formal “Hello” or “Greetings” might be fine instead of “Dear.” But use discretion and be certain that the workplace culture is relaxed enough.
In some instances, it’s difficult or impossible to identify your cover letter recipient.Failing your best efforts to come up with a name, or even a position title, try a greeting along these lines: “Dear Cybersecurity Analyst Hiring Team” or “Dear Cybersafe Solutions Group.”
The goal of the cover letter greeting: Connect directly with the employer in a manner that’s professional but friendly.
Cover letter introduction
Communication comes with the territory of cyber security professionals, who are expected to interact with managers, colleagues, clients, and all manner of stakeholders. No matter how technical and complex the subject matter is, you must make it relatable.
Your on-the-job adeptness from all sides of human and computer interfaces can come across in your cover letter introduction. Put this hiring organization at the forefront of your value proposition, using energetic language to convey that:
- A blend of solid IT knowledge and cybercrime-fighting experience make you an ideal fit for this job.
- You are excited about the opportunity to work for this employer.
- The employer stands to benefit from hiring you in this vitally important cyber security role.
The goal of the cover letter introduction: Intrigue the reader enough to learn more about your strongly matched qualifications as a cyber security specialist
Here’s the greeting and introduction from our cyber security cover letter sample.
Dear Mr. Warwick,
With five years of system administration, network optimization, and cyber security experience at two blue-chip organizations, I am ready to take the step to a consultancy role.
Cover letter middle part (body)
These cover letter middle paragraphs are where you back up your introductory pitch for being an excellent cyber security candidate. Further, implement your custom-tailoring strategy by choosing a few relevant career highlights. Your selectivity should guide everything you’ve learned about the job requirements and the employer’s needs and goals. Show that you understand the organization’s greatest concerns and challenges, while helping the hiring manager picture you in a vital problem-solving role.
Reframe your work history examples as achievements, emphasizing measurable outcomes wherever possible. Include facts and figures to substantiate your track record of cyber security wins, both on the prevention and recovery side. Incorporate an anecdote or two, or give a sense of your passion and purpose.
The goal of the cover letter body: Elaborate on how this employer would benefit from your contributions as a proficient and conscientious cyber security specialist.
Our cyber security cover letter sample illustrates what you might include in the middle part:
While much of my career thus far has focused on troubleshooting and risk management, I have enjoyed lead roles in major strategic projects. For example, we reduced downtime due to cyber-attacks by 35% thanks to an employee awareness course. Cyber security is as much about influencing behaviors as it is about fighting malware and hacks. Embedding such behaviors is a critical approach for any consultancy.
I am an experienced trainer in all aspects of operational cyber security and enjoy passing on my knowledge to others. I have run 200+ training sessions and enjoy shocking attendees with real-world examples of what happens when cyber security goes wrong. I wish to join a consultancy because it allows me to widen my impact.
My complete certifications and qualifications are outlined in my resume, but the following should offer a reasonable window on my proficiency:
Knowledge: Anti-Virus, RSA security, ID/PS, Full Packet Capture, Host-Based Forensics
Certifications: SANS GIAC/GCIA/GCIH, CISSP, and SIEM-specific training
Architecture: Nitro/McAfee Enterprise Security Manager, ArcSight, QRadar, Splunk
Signature development: YARA, Snort, HIPS
Every project that I have led has been run on agile principles. I have enjoyed the intellectual challenge of working out seemingly impossible problems. One of our projects was even nominated for “Process Improvement of the Year” by CyberTech magazine.
Cover letter closing
You can now end your cyber security cover letter with a signal that communication with this employer has only just begun. A call to action in your cover letter closing leaves the door open for hiring managers to get back to you. The intent is to make it less easy or comfortable for the employer to set your application aside and forget about it.
How? You might propose further discussion during an interview, or even during an on-site visit. Express an interest in learning more about the organization’s cyber security issues on such an occasion. For a more reserved call to action, merely indicate you are looking forward to a response.
It’s a good idea to briefly recap your best case for being a great job candidate, adding a note of thanks for the recipient’s time and attention.
Then, simply sign off with “Sincerely,” Best regards,” or “Best,” above your name.
The goal of the cover letter closing: End on a confident, upbeat note with a call to action that carries an expectation of the employer following up.
Below is the closing section of our sample cyber security letter.
I am excited to learn more during a potential interview and look forward to hearing about what you hope to achieve with your clients over the coming years.
Sincerely,
Landon Parks
Common cover letter mistakes — zero tolerance
Employers will expect nothing less than 100% bug-free results from your cyber security cover letter. These are some of the most common errors that could crash your chances.
- Sending the same generic cover letter with multiple job applications, with no effort to personalize or custom-tailor the address or content
- Word bloat — repetition, rambling on, meaningless clichés, and fluffy filler language
- Overemphasizing your technical expertise, at the expense of communication and interpersonal strengths
- Preventable and correctible typos, spelling mistakes and grammatical gaffes
- Over-reliance on spell-check and grammar apps that fail to catch other problems like inconsistent capitalization, periods ending bullet points, date formats and such
- Document design deficiencies and flawed formatting
Looking for a failsafe way to create a spotless, terrific-looking cover letter? Free yourself to focus on the content by leaving the layout, design, and formatting details up to Resume.io. Choose one of our field-tested cover letter templates. Then, drop in your own replacement text using our online builder tool.
Key takeaways for a cyber security cover letter
- Exceptionally rapid employment growth for cyber security professionals makes a stand-out cover letter essential to pursue the most rewarding, best-fitting positions.
- The narrative style of a cover letter lends itself to telling the kind of problem-solving success stories that prospective employers can identify with.
- Each cover letter section reinforces your connection with hiring managers by directly addressing the employer’s cyber security requirements.
- Be sure not to overlook the value-added interpersonal strengths that make you an outstanding cyber security specialist
- Your cover letter must be as bug-free as the computer network infrastructure you design and configure.
For additional inspiration, you can check out these other cover letter examples for IT occupations:
- Software Engineer cover letter sample
- IT cover letter sample
- Graphic Design cover letter sample
- Programmer cover letter sample
- Data Analyst cover letter sample
- Software Developer cover letter sample
- Google cover letter sample
- Data Scientist cover letter sample
- IT Manager cover letter sample
- System Administrator cover letter sample
- Apple cover letter sample
- Software Tester cover letter sample
- Data Entry cover letter sample
- Computer Science cover letter sample
- Scrum Master cover letter sample
- DevOps Engineer cover letter sample
- IT Director cover letter sample
- Full Stack Developer cover letter sample
- IT Project Manager cover letter sample
- UX Designer cover letter sample
- IT Technician cover letter sample